Imagine it is 8 AM on a Monday. A hacker doesn’t steal credit card data; instead, they send a single command that shuts down your city’s entire EV charging network. Commuters are stranded. Your fleet customers are paralyzed. Your brand’s reputation evaporates in minutes. This isn’t science fiction. It is the real-world risk facing unprepared charge point operators today.
The conversation around electric vehicles has focused on range, speed, and cost. Now, the most important conversation is about security. Strong EV Charging CyberSecurity is no longer just an IT issue; it is a fundamental requirement for business survival. With the cost of cybercrime projected to reach $13.82 trillion annually by 2028, according to Statista, ignoring this threat is a critical business failure.
This guide is for the leaders, engineers, and security professionals responsible for building and protecting our electric future. We will move beyond theory to provide a clear, actionable framework for defending your charging infrastructure. We will cover the attack surface, the top threats, and the layered defense strategy you need to implement now.
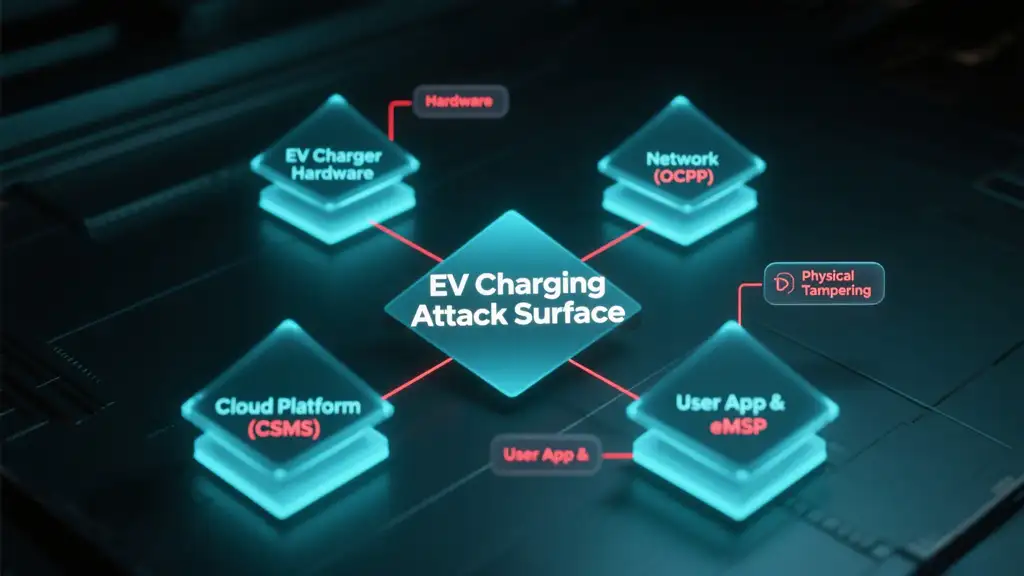
An EV charger is not just a power outlet. It is a sophisticated, internet-connected computer—an IoT device. To protect the system, you must first understand its components. The EV Charging CyberSecurity attack surface can be broken down into four key domains.
1. The Charger (The Edge) The physical Electric Vehicle Supply Equipment (EVSE) is your frontline. Attackers can target it with physical tampering to install malicious hardware or exploit vulnerabilities in its firmware to take control of the unit.
2. The Network (The Connection) Chargers constantly communicate with a central management system over the internet, typically using the Open Charge Point Protocol (OCPP). This connection is a prime target for Man-in-the-Middle (MITM) attacks to steal data or Distributed Denial of Service (DDoS) attacks to knock chargers offline.
3. The Backend (The Cloud) The Charging Station Management System (CSMS) is the brain of your network. A breach here could be catastrophic. Attackers can target the CSMS to steal user data, manipulate pricing, or gain control over your entire network of chargers.
4. The User & eMSP (The Human Element) The driver’s mobile app and the complex web of eMobility Service Provider (eMSP) roaming agreements create more potential entry points. Phishing attacks on users or compromised APIs between partners can grant a hacker access to the ecosystem.
Understanding vulnerabilities is important. Understanding how they impact your bottom line is essential. A technical threat only becomes a business priority when you calculate its cost in revenue, reputation, and liability. Here are the top threats to EV charging network security and what they really mean for your business.
| Threat | Technical Description | Real-World Business Impact |
|---|---|---|
| Network Interruption (DDoS) | An attacker floods your chargers or central management system with junk traffic, making them unable to respond to legitimate users. | Immediate Revenue Loss: Your entire network stops generating money. Brand Damage: Drivers see your brand as unreliable. SLA Violations: You fail to meet uptime promises to your fleet customers and partners. |
| Unauthorized Control (CMS Backdoor Breach) | A hacker gains administrative access to your CSMS backend through stolen credentials or a software vulnerability. | Grid Destabilization: An attacker could turn thousands of chargers on or off at once, threatening the local power grid. Total Revenue Hijack: Prices could be set to zero, or payments redirected. Complete reputational collapse. |
| Data Interception (MITM) | An attacker secretly intercepts the communication between a charger and the backend, reading or altering the data being sent. | Massive Data Breach: Theft of driver personal information and payment details. Huge Compliance Fines: Fails PCI DSS for payments and privacy laws like GDPR/CCPA. Lawsuits and loss of customer trust. |
| Firmware Hijacking | A malicious actor replaces the charger’s legitimate software (firmware) with their own version. | Creation of a “Botnet”: Your expensive hardware assets are turned into a network of zombie computers to attack others. Physical Damage: Malicious firmware could potentially damage the charger or a connected vehicle. Bricking of Assets: Renders hardware useless, requiring costly manual replacement. |
| Payment Fraud | Attackers exploit weaknesses in the payment system, either by cloning RFID cards or intercepting payment data. | Direct Financial Loss: You are responsible for fraudulent charges. High Transaction Fees: Payment processors may increase your fees or drop you as a client due to high chargeback rates. Loss of driver confidence. |
Technical Description: An attacker floods your chargers or central management system with junk traffic, making them unable to respond to legitimate users.
Real-World Business Impact: Immediate Revenue Loss: Your entire network stops generating money. Brand Damage: Drivers see your brand as unreliable. SLA Violations: You fail to meet uptime promises to your fleet customers and partners.
Technical Description: A hacker gains administrative access to your CSMS backend through stolen credentials or a software vulnerability.
Real-World Business Impact: Grid Destabilization: An attacker could turn thousands of chargers on or off at once, threatening the local power grid. Total Revenue Hijack: Prices could be set to zero, or payments redirected. Complete reputational collapse.
Technical Description: An attacker secretly intercepts the communication between a charger and the backend, reading or altering the data being sent.
Real-World Business Impact: Massive Data Breach: Theft of driver personal information and payment details. Huge Compliance Fines: Fails PCI DSS for payments and privacy laws like GDPR/CCPA. Lawsuits and loss of customer trust.
Technical Description: A malicious actor replaces the charger’s legitimate software (firmware) with their own version.
Real-World Business Impact: Creation of a “Botnet”: Your expensive hardware assets are turned into a network of zombie computers to attack others. Physical Damage: Malicious firmware could potentially damage the charger or a connected vehicle. Bricking of Assets: Renders hardware useless, requiring costly manual replacement.
Technical Description: Attackers exploit weaknesses in the payment system, either by cloning RFID cards or intercepting payment data.
Real-World Business Impact: Direct Financial Loss: You are responsible for fraudulent charges. High Transaction Fees: Payment processors may increase your fees or drop you as a client due to high chargeback rates. Loss of driver confidence.

There is no single “magic bullet” for EV Charging CyberSecurity. A robust defense requires multiple layers of security working together. If one layer fails, another is there to stop the attack. This is a practical, five-layer framework you can implement to protect your assets.
Your defense starts at the physical charger.
Use Tamper-Proof Enclosures: The physical design should prevent unauthorized access to internal components.
Implement Secure Boot: This ensures that the charger will only ever load software that is cryptographically signed by you, the manufacturer. It makes firmware hijacking significantly more difficult.
Utilize a Trusted Platform Module (TPM): A TPM is a dedicated microchip that securely stores cryptographic keys, certificates, and other secrets, keeping them safe from software-based attacks.
The data flowing between your chargers and the cloud must be protected.
Mandate Encrypted Communication: All network traffic must use Transport Layer Security (TLS) version 1.2 or, preferably, 1.3. This encrypts the data so it cannot be read if intercepted.
Use a Virtual Private Network (VPN): A VPN creates a secure, private tunnel over the public internet for each charger. This shields the charger from being directly exposed to network scans and attacks.
Implement Network Firewalls: Configure firewalls at both the charger (if possible) and the cloud entry point to block all unauthorized traffic.
Your central management system is your crown jewel and must be defended as such.
Enforce Strong Access Controls: Implement Multi-Factor Authentication (MFA) for all administrative users. Use Role-Based Access Control (RBAC) to ensure employees can only access the systems they absolutely need for their jobs.
Conduct Regular Security Audits: Hire third-party penetration testers annually to actively try to hack your system and find weaknesses before criminals do.
Encrypt Data at Rest: All sensitive customer and operational data stored in your databases must be encrypted.
You don’t have to invent security from scratch. Build on the work of global standards bodies.
Adopt OCPP 2.0.1: The latest version of the Open Charge Point Protocol has robust security features built-in, including secure firmware updates, security event logging, and certificate management. Insist on it for all new hardware.
Implement ISO 15118: This standard enables the highly secure “Plug & Charge” feature. It uses a Public Key Infrastructure (PKI) to create a secure, authenticated identity for the vehicle itself, eliminating the need for RFID cards or apps.
Maintain PCI DSS Compliance: If you handle credit card data, you must adhere to the Payment Card Industry Data Security Standard. This is a non-negotiable requirement to protect against payment fraud.
Technology is only part of the solution. Your people and processes are the final, critical layer.
Establish a Security Operations Center (SOC): You need 24/7 monitoring of your network to detect and respond to threats in real-time. This can be in-house or outsourced.
Develop an Incident Response Plan: What do you do when an attack happens? Who do you call? How do you communicate with customers? This plan must be documented and practiced before you need it.
Train Your Staff: The most common entry point for hackers is a human one. Conduct regular training for all employees on phishing, social engineering, and password security.
In the rapidly expanding world of electric mobility, EV Charging CyberSecurity cannot be an afterthought. It is not a cost center to be minimized; it is a foundational investment that enables growth, builds trust, and protects your entire business.
The threats are real and carry significant financial and reputational consequences. However, by adopting a proactive, layered “Defense-in-Depth” strategy, you can build a resilient, secure, and trustworthy network. The operators who prioritize security today are the ones who will lead the market tomorrow. They will win the largest customers, build the strongest brands, and own the future of electric transportation.
Authoritative Sources
U.S. Department of Energy – Securing EV Charging Infrastructure Series: This is a direct article from the Office of Cybersecurity, Energy Security, and Emergency Response (CESER) on the specific topic, making it highly relevant.
NIST (National Institute of Standards and Technology) – The Cybersecurity Framework Homepage:
Vi invieremo informazioni tecniche dettagliate e un preventivo!